S3 Ransomware – how it occurs and how to prevent

S3 Ransomware – how it occurs and how to prevent
One needs S3 buckets to host Javascript UI or to store business data, application logs and backups, customer-provided data, and so on. An outage of the S3 bucket may cause business interruption and thus lead to loss of revenue, failure of operations, and loss of reputation. While there are mechanisms to detect and prevent data exfiltration from S3, a ransomware attack is difficult to detect and mitigate (if successful). An S3 ransomware attack is an issue of grave concern because the attack vectors facilitate the capture of confidential data and allow it to hold your data for ransom.

How it occurs
Data in a bucket is encrypted or re-encrypted with an object-key and that object-key itself is encrypted by a master-key. While master-key is freely available to perform encryption, its access is denied for decryption. Only a ransom note file is left in an unencrypted state. Only the attacker has access to the master-key required for decryption. Bucket owner’s data resides in the bucket with the data-key; however the data-key is encrypted with the master-key. The attacker offers access to the master-key for decryption if the victim fulfils ransom demand. Attacker uses his/her own or another compromised AWS account’s master-key. The master-key can be marked for deletion (minimum 7 days wait time) and the attacker can give that timeline to the victim to fulfil ransom demand. This 7 days window can be reduced however we will not reveal that method here. This attack can happen so fast that by the time, the victim detects the attack (even if a few minutes), significant damage has already been done. In summary, an attack is successful if- Objects in S3 have been encrypted by an object-key that cannot be decrypted
- There is no other copy of retrievable objects. It may also include the scenario that recovering data from other copies is impractical.
How To Prevent S3 Ransomware Attack
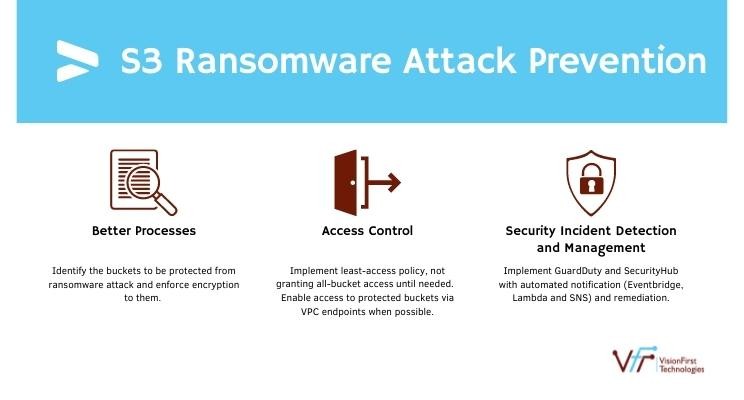
Better Processes
- Identify the buckets which should be protected from S3 Ransomware attack and the ones that need not be protected. Implement prevention plan for protected buckets and mitigation plan for other buckets.
- Enforce encryption on protected buckets. You may also set the default encryption key.
- Preferably, use Customer Managed Key (CMK) of KMS instead of AWS Managed Key to encrypt data in a protected bucket. You may implement resource based policies on CMK to restrict its usage.
- Implement Multi-factor authentication delete for protected buckets. Please note that this feature can be enabled by root user only.
- Implement bucket versioning. It may preserve earlier accessible objects. However, this may lead to EDoS attacks (Economic Denial of Sustainability) provided other prevention mechanisms are not implemented.
- Backup data of protected bucket. However, this is a costly proposition because with backup your storage cost may double. Nonetheless, S3 has cheaper storage options such as S3 Glacier.
Access Control
- Implement least-access policy. Do not grant all-buckets access until absolutely required.
- Disable public access of all the buckets at the account level. If you must grant public access on certain buckets then create a separate account that may grant public access to certain buckets.
- If granting public upload of objects access then upon upload, re-encrypt objects to ensure that only the objects that can be decrypted have been stored in the bucket.
- Enable access to protected buckets via VPC endpoints if possible. It will further restrict access to buckets.
- Implement access point of buckets rather than direct bucket access. It is one way of obfuscating bucket names and enforcing additional access policies.
- Enforce Service Control Policy to deny using KMS key that does not belong to trusted AWS account(s). It will require you to set up AWS Organizations or AWS Control Tower. The benefits that AWS Control Tower brings is immense to streamline your AWS infra management, financial management, security and separation of duties.
Security Incident Detection and Management
- Implement GuardDuty and SecurityHub with automated notification (Eventbridge, Lambda and SNS) and remediation. You may consider implementing a SIEM solution to have a holistic view of your IT landscape security.
- Protect other AWS services such as EC2 instances. Attacks on these services can quickly lead to attacks including S3 Ransomware attack. Implementing GuardDuty and SIEM can help you detect those attacks early.
- Implement Security Incident Management Processes - 1. Preparation, 2. Detection and Analysis, 3. Containment, Eradication, and Recovery, 4. Post-Incident Activity
Conclusion
If an attack has been initiated then you have very less time to prevent the damage. If an attack is successful then it can be very damaging with no guarantee of data recovery. Thus, it is better and easier to implement prevention mechanisms.Recent Posts
visionfirst0 Comments
Decoding Business Intelligence Architecture For Informed Decision Making
visionfirst0 Comments
What is BI (Business Intelligence)?
visionfirst0 Comments
S3 Ransomware – how it occurs and how to prevent
Tags
aws advanced partner
aws consulting partner
aws partner
aws select partner
aws service provider
aws technology
azure consulting partner
azure partner
azure service provider
business intelligence architecture
cloud architecture
cloud bi solutions
cloud security provider business intelligence consulting company aws managed security services business intelligence financial services
Related Blogs
visionfirst0 Comments
Information Security Compliance for Financial Services Companies in the US
Companies offering financial services need to promote a strong compliance culture to nurture a community
visionfirst0 Comments
GDPR – Let’s implement
General Data Protection Regulation (GDPR) is applicable as of May 25th, 2018 in all member
visionfirst0 Comments
Decoding Business Intelligence Architecture For Informed Decision Making
Your business decisions seem to depend on high-quality data and information. But in today’s highly







