Confidential Computing – Capture SSN and Store Safely

Confidential Computing – Capture SSN and Store Safely
Sharing confidential information with someone else but also having an assurance that the information will be used only as per your wish is the essence of Confidential Computing. A concept developed by the Confidential Computing Consortium, a community that advocates data security to make projects immune to breaches, Confidential Computing is emerging as a necessity for almost all sectors today.
A very common example of how Cloud Computing has started influencing our everyday lives is that whenever we allow our Social Security Number (SSN) or credit card numbers to be captured on screen, access is not granted to any person working in the backend (not even application developers or support engineers) to extract this information by any means. This way, we not only ensure that our data is being shared with the right platform but also make sure that our data is used for only the permitted purpose.
Data Confidentiality As Per Law
The law in itself has been supportive of such confidentiality in public systems. Federal Information Processing Standards (FIPS) for instance, has sections F197, F200, F201, etc., that lay down guidelines for Advanced Encryption Standard (AES), Minimum Security Requirements, and Personal Identity Verification (PIV) of employees so that everything, from sharing to access of data, is regulated and confidential. Other confidentiality laws such as PCI-DSS, HIPAA, etc. also reinforce the same.
It is quite evident that the security of data has to be preserved at all stages of transfer and processing. Therefore, as per law, organizations asking for such data must first put in place an architecture that ensures stringent confidentiality and meets the requirements of compliance as per PCI-DSS, HIPAA, etc.
Confidential Computing Architecture
To give you a better idea of how a system can be made robust enough to offer adequate confidentiality, here are the two steps of secure architecture.
Confidential Data from Capture to Storage
When a user enters his/her sensitive data such as SSN number or credit card number on screen, rendered using Cloudfront, the sensitive field is encrypted using one of the following methods:
- Cloudfront field-level encryption or
- Lambda@edge
Both methods use Public Key to encrypt sensitive data. As you might know about asymmetric keys (public-private key), data encrypted by one key can be decrypted by only the other key. So, the data encrypted by public key can be decrypted by corresponding Private Key only.
$ aws kms generate-data-key-pair-without-plaintext –key-id alias/app/secured –key-pair-spec ECC_NIST_P256
{
“PrivateKeyCiphertextBlob”: “AQIDAHiLNriWT44xph+pts2CUNIhXlx9w5+KpQib+9Bv5v/aLgEACEEPkCHkg+Zxes0QW8ODAAAA+TCB9gYJKoZIhvcNAQcGoIHoMIHlAgEAMIHfBgkqhkiG9w0BBwEwHgYJYIZIAWUDBAEuMBEEDCTuDxzatu1N909iSQIBEICBsUteXWpBx9sib+W4LCKzNssimGux0tRrNT1zVubplFEHJEFgffZjeoq0cxzpyn1PWKaW2tk56NLSjrRmudtTE4bTDBavUKgOZloEbn2jklGVeGMeqzJtdihz+Z13P7mq1ju+0WnFdfFg1WeXpfu1NuoIgbxEd/vJJNap2fhCUzAM/CSzEAwANzI9b/vF8xthBcJOQ1m5+lZ/97h57WAa0PVxvE4ZfsSMaWSsQedvsoaUOw==”,
“PublicKey”: “MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEqC0Q3wDGQ1YCf5atEFZ0pXmq/yEjyf9QwQhxXrQr39IylSpd5pt/KYcZrwRHrl7WOtd7UD7uO5a9Amt++Aa0/w==”,
“KeyId”: “arn:aws:kms:us-east-1:1234567890:key/61840ad8-1123-4f6a-b870-fb88dae7025c”,
“KeyPairSpec”: “ECC_NIST_P256”
}
Private Key generated above can be stored in any data store in encrypted form. 3
Upon form submission, the encrypted data traverses from Cloudfront to an ec2 instance which has Nitro Enclave.
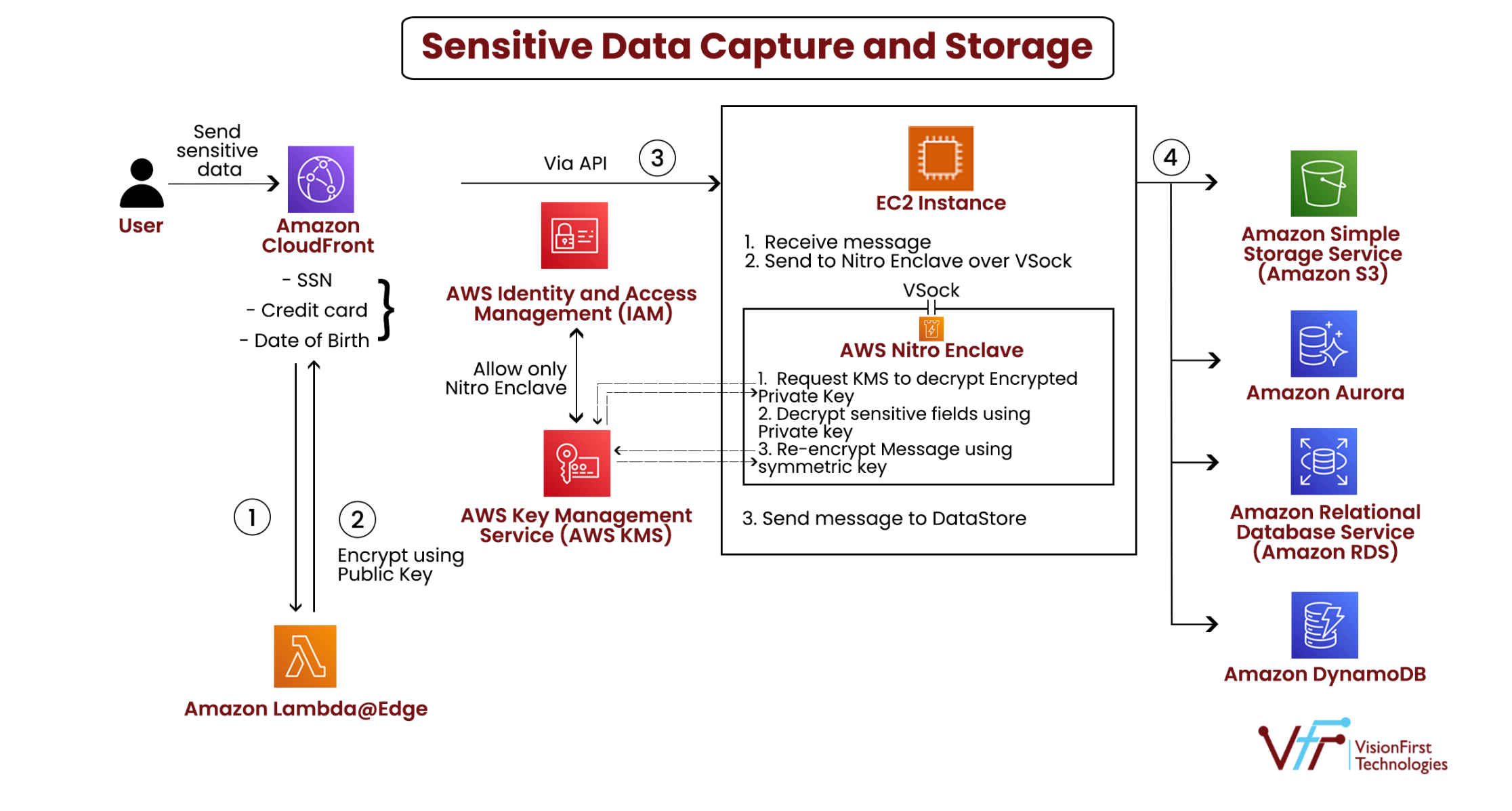
Ec2 instance host sends the message with sensitive data and encrypted private key to Nitro Enclave through VSock proxy. Nitro Enclave requests KMS to decrypt the private key and the decrypted private key flows to Nitro Enclave over TLS.
Nitro enclave can then re-encrypt sensitive data using another KMS Symmetric key. Re-encryption ensures that the data can be decrypted now and in future. Additionally, Nitro enclave can anonymize/tokenize sensitive data.
This re-encrypted and tokenized data can be stored safely in any data store such as S3, Dynamo DB, RDS, Aurora DB.
Revealing Sensitive Data to Authorized Users
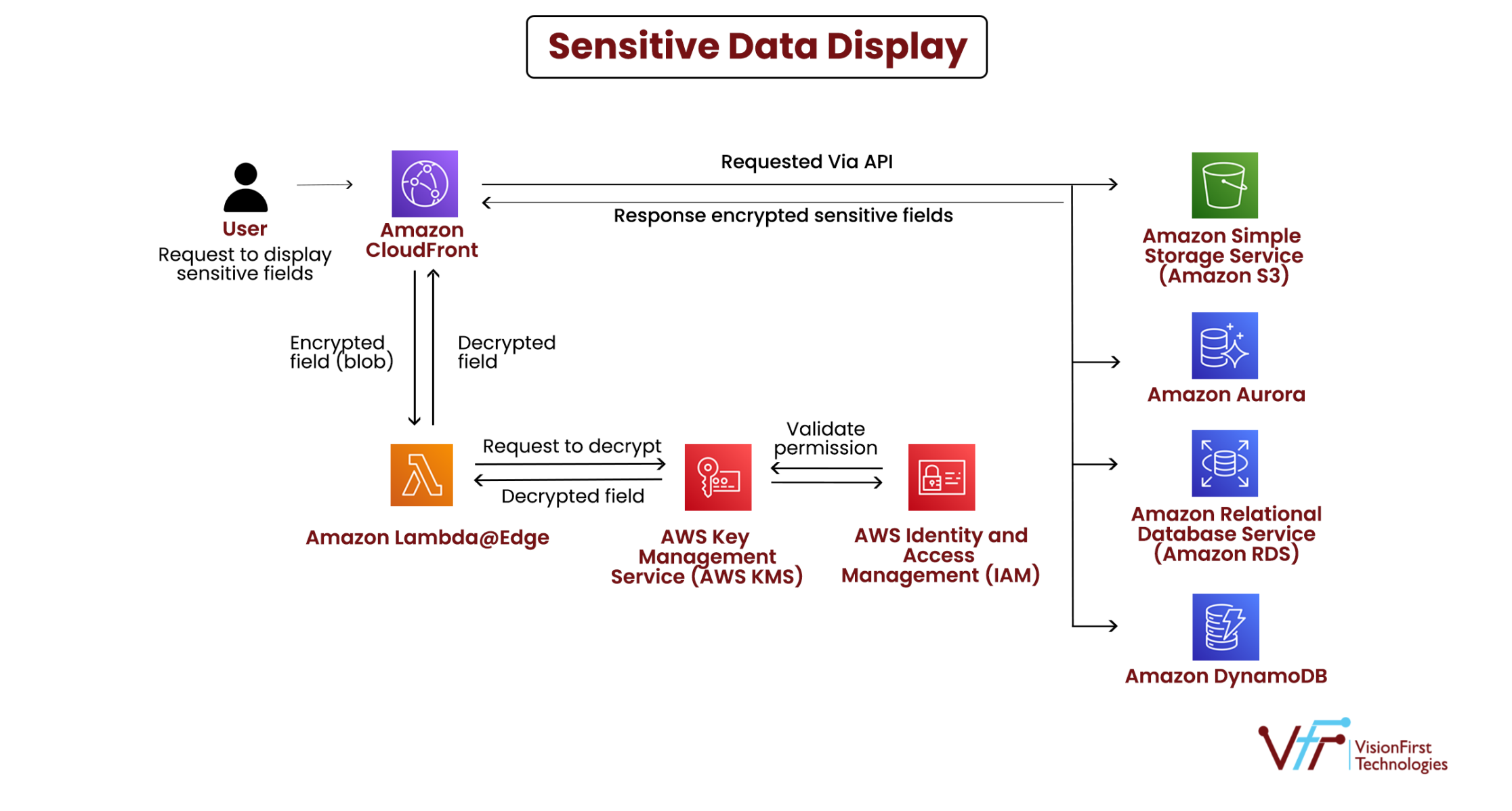
Now when authorized users make requests to view the masked fields, Cloudfront forwards the request to Lambda@edge from where a field decryption request is sent to Key Management System (KMS). The Attribute-Based Access Control (ABAC) of IAM then determines whether access rights can be provided based on the set access control paradigm. If the request gets authorized, the decryption is completed and CloudFront displays the information in the given field.
Since request is decrypted at edge location, the plaintext sensitive field cannot be logged in access logs and chances of plaintext sensitive data displayed to an unauthorized user is greatly reduced.
Conclusion
While Confidential Computing is a compliance requirement for regulated industries such as finance and healthcare, it is always good to implement Confidential Computing to preserve confidentiality of sensitive data for any industry. It imbibes the confidence in your customers of doing business with you and protects organizations from costly lawsuits.








