Practical Guide to creating AWS site to site VPN
Practical Guide to creating AWS site to site VPN
In our article Cloud – an extension to your infrastructure, we discussed about different network topologies to tame cloud infrastructure to enhance your organization’s infrastructure. The first topology “Cloud is only an extension of your office network” surely needs site-to-site VPN while other topologies may utilize site-to-site VPN for most convenient and secure access to AWS infrastructure.
In this article, we will give you practical approach to creating site-to-site VPN from your office LAN to AWS.
Equipment used
Before we get into details, please find below the equipment used:
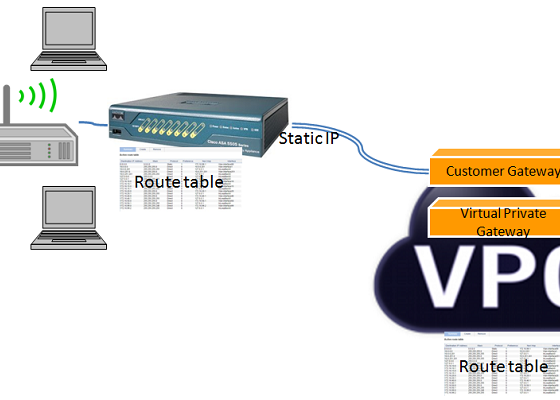
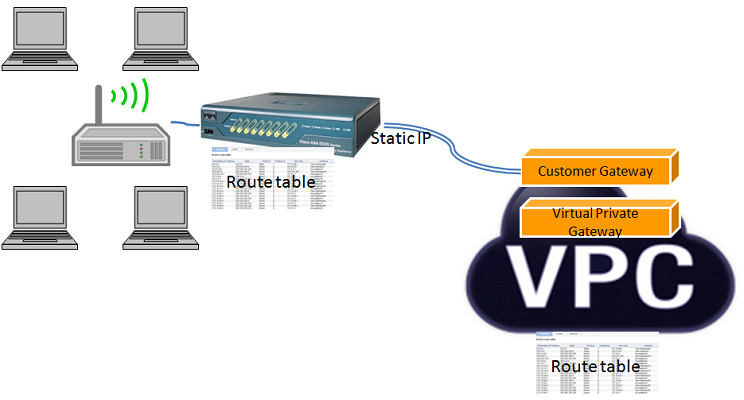
- Cisco RV042 Switch
- Belkin Wireless Router
- On-premise LAN established by Wireless router
- Private and Public Subnet of VPC on AWS
Configuring the networks
Note down static IP from your Internet Service Provider (ISP) to your switch. That IP should show towards WAN portion of your switch.
On AWS side
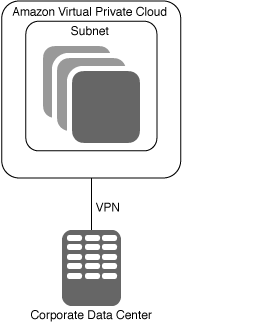




- Create a VPC with two or more subnets, having a Virtual Private Gateway and Internet Gateway.
- Create Customer Gateway with static IP noted in above step.
- Create Site-to-site VPN tunnel using above Virtual Private Gateway and Customer Gateway.
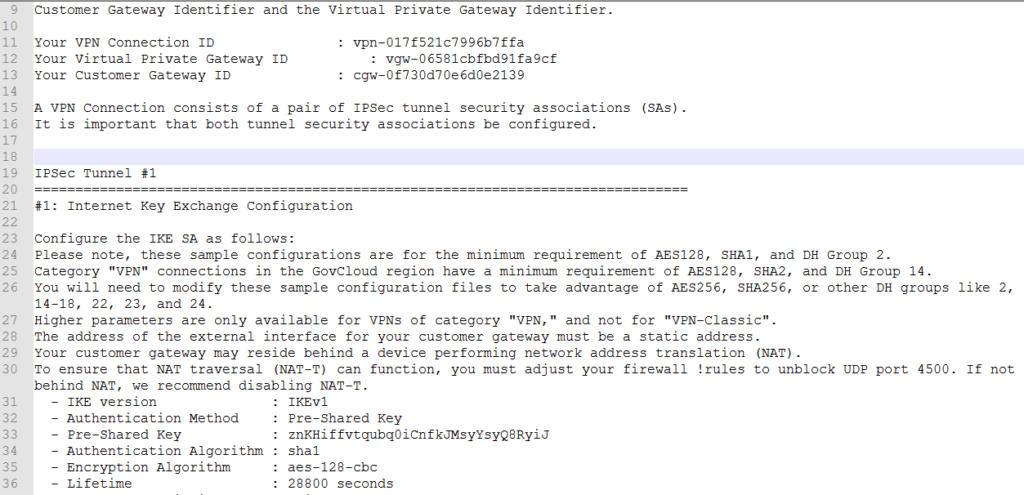
- Download configuration appropriate for your switch. If you are unsure then download generic configuration.
- The configuration file will contain external IP of the two tunnels, Pre-shared Key, encryption algorithms and other information to establish connectivity.
- Create a security group that allows inbound and outbound connectivity from and to on-premise subnet(s).
- Establish route from subnet to on-premise network. Please note that there must not be an overlap of IP from AWS site to on-premise site.
- The destination of route from AWS site to on-premise site should be Virtual Private Gateway.
- The destination of route from AWS site to AWS Virtual Machines should be local.
- The destination of route from AWS site to other locations (internet) should be Internet Gateway. Internet Gateway should not be set for Private Subnet route.
On on-premise side


- Create site-to-site VPN tunnel on your switch. You will need configuration information collected when creating site-to-site VPN at AWS site. Setting this up is easy.
- Establish firewall rules to permit traffic coming from AWS subnet to on-premise network.
- Establish mapping of NAT to permit traffic coming from AWS subnet to reach to corresponding private ports in LAN.
Let’s test
On-premise to AWS connectivity testing
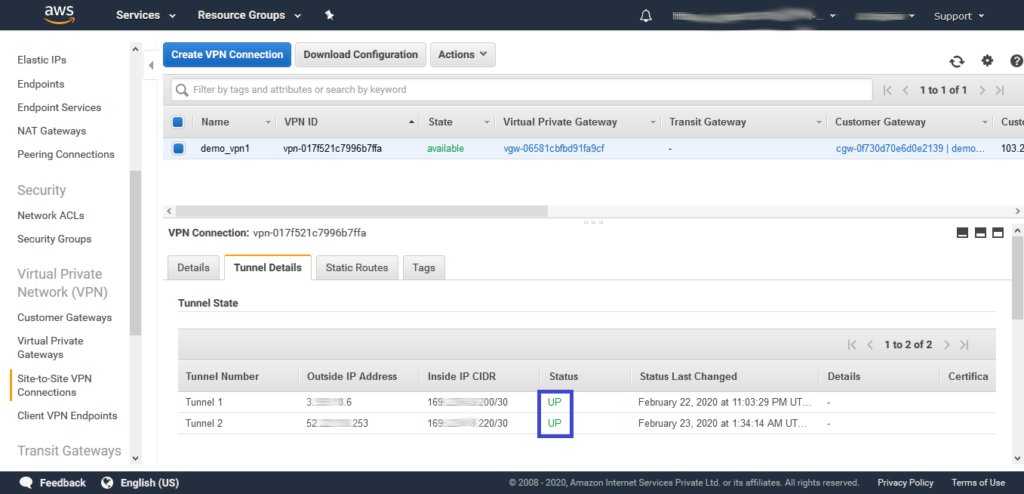
- Create an ec2 instance in AWS in a private subnet.
- Establish a session via putty from on-premise machine to ec2 instance via its internal IP. If you can login then connectivity from on-premise to AWS has been established.
- Try the similar for an ec2 instance in AWS in private subnet.
- If the connectivity does not establish on either subnet then the issue is most likely security group too restrictive or route needs to be fixed. Network ACL can also be the culprit, however, default network ACL permit all traffic so it may not be an issue when establishing connectivity.
Did you notice that the VPN tunnels are up after this operation? Please note that network traffic must be generated from on-premise to bring up VPN tunnel so this testing must be done first.
AWS to on-premise testing

- Start a service on one of the machine in LAN. The service can be an nginx server or Flask server listening to requests. For our test, we chose Flask server.
- Ensure that Switch and Route permit connectivity from AWS to on-premise LAN and that particular IP and port.
- Access the on-premise IP and port service via an instance in ec2 (Windows or Linux) in AWS. The curl request works.
Back to you
Was that easy? Establishing the clear line of sight requires diligence and surely is error prone. When that happens, you need to get your hands dirty and check the whole sequence.
Do you use some best practices so that it works on the first attempt every time? Start the conversation.
About VisionFirst Technologies Pvt. Ltd.
We are a group of researchers and practitioners of cutting edge technology. We are AWS Registered Partner. Our tech stack includes Machine Learning, offline/2G tolerant mobile apps, web applications, IOT and Analytics.