Strengthening Cloud Resilience: How an Enterprise Achieved Enhanced Security and Observability on AWS

Strengthening Cloud Resilience: How an Enterprise Achieved Enhanced Security and Observability on AWS
Executive Summary
A large Insurance service provider in India relied heavily on AWS but faced pressure to formalize their security posture, eliminate information security risks, and bring predictability to their volatile cloud spending.
VisionFirst Technologies implemented a comprehensive, phased solution centered on AWS Control Tower, GuardDuty, and Security Hub. The project successfully established a resilient, multi-account architecture that resulted in zero critical security findings and immediate financial predictability through robust cost anomaly detection
1. The Challenge
The customer managed business-critical applications on AWS but lacked centralized governance and full observability necessary for long-term cloud maturity
| Area | The Problem |
| Security Risk | Lack of centralized account governance and continuous threat detection led to high information security risks and undefined security posture. |
| Cost Volatility | The absence of proactive monitoring and financial guardrails resulted in unpredictable and often high cloud bills, making budgeting difficult. |
| Architecture | Environments lacked proper segregation, increasing the complexity of managing Production, Non-Production, and core security functions. |
| Operations | Security incident management was reactive and ad-hoc, without a defined framework for analysis, notification, and remediation. |
2. The Solution
We proposed a strategic, phased engagement focused on establishing a secure, scalable AWS landing zone using native security and governance tools.
The implementation was structured into four key phases:
- Tool Implementation
- Account Migration
- Observability Setup
- Continuous Improvement
A. Foundational Architecture and Governance
The core of the solution was establishing the right foundation using the AWS Control Tower.
- Multi-Account Structure: The existing account was restructured into a new Organizational Unit (OU) hierarchy, creating dedicated accounts for: Management, Production, Non-Production, Log Archive (centralized logging), and Security Tooling. This clear segregation improved security and management efficiency.
- Enforced Guardrails: Control Tower was used to apply mandatory and proactive guardrails, such as disallowing the deletion of critical log archives and restricting resource creation to specific, approved regions.
B. Core Security and Detection Implementation
A comprehensive suite of AWS security services was deployed across the new accounts:
| Tools | Purpose and Function |
| AWS Security Hub CSPM | Centralized security posture management (CSPM); ran continuous checks against standards like CIS Foundations and AWS Foundational Security Best Practices. |
| Amazon GuardDuty | Continuous threat detection, monitoring AWS accounts and workloads for malicious activity. |
| Amazon Inspector | Automated vulnerability management, scanning EC2 instances and containers for software vulnerabilities. |
| AWS WAF | Deployed on services (CloudFront, load balancers) to protect against common web exploits and bots. |
| AWS CloudTrail | Enabled across all accounts and regions to ensure non-repudiable logs were collected and stored centrally in the Log Archive Account for forensics. |
C. Observability and Cost Governance
An operational framework was implemented to ensure active monitoring and financial health:
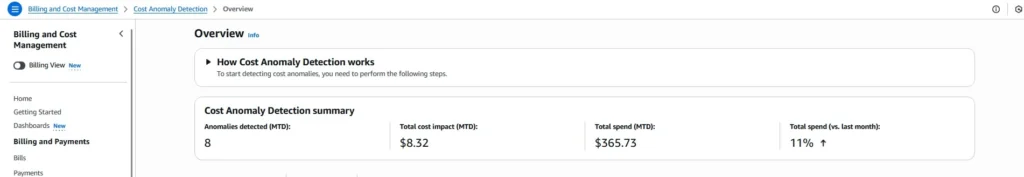
- Financial Guardrails: AWS Budgets and Cost Anomaly Detection were set up to provide real-time alerts (including SMS for critical breaches) when spending crossed predefined thresholds (e.g., 50%, 100%).
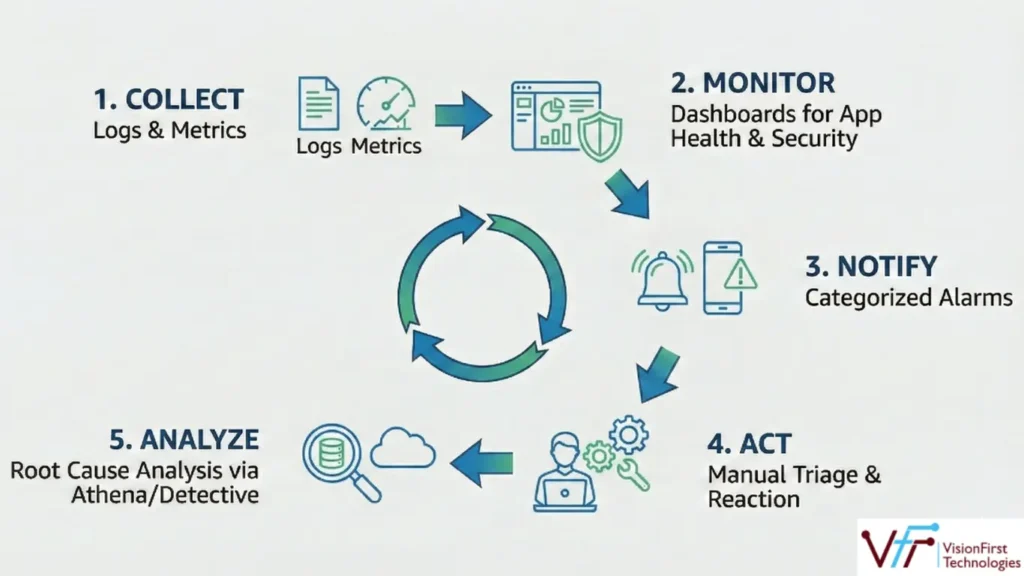
- Observability Framework: The five-step operational cycle was established – Collect (logs and metrics), Monitor (dashboards for application of health and security), Notify (categorized alarms), Act (manual triage and reaction procedures), and Analyze (root cause analysis via Athena/Detective).
3. Results and Business Impact
The project successfully delivered a secure, well-governed, and financially predictable cloud environment, moving the client from a reactive stance to proactive cloud operations.
A. Security and Compliance Achieved
- Zero Critical Risk: Upon implementation and auditing, the environment achieved zero critical security findings on its active production and development resources, validating the success of the new control framework.
- Instant Visibility: Security Engineers gained access to the Security Tooling Account, providing integrated findings from GuardDuty, Inspector, and Security Hub.
- Resilience: The implemented IAM hardening, including password and MFA policies, significantly reduced the risk of identity-based attacks.
B. Architectural Success and Scalability
- 100% Migration Success: The complex migration of existing applications into the new multi-account structure was completed successfully and without downtime, establishing a scalable foundation ready for future application development.
- Simplified Access: Centralized identity management via AWS IAM Identity Center simplified the user experience while enforcing least-privilege access across all environments.
C. Operational and Financial Predictability
- Proactive Cost Management: The use of Cost Anomaly Detection and threshold-based budget alerts (SMS and email) immediately eliminated unexpected high bills, giving financial controllers peace of mind and allowing for accurate, forward-looking financial analysis.
- Defined Operations: The establishment of the Collect, Monitor, Notify, Act, and Analyze framework provided a structured, repeatable, and auditable process for managing security and operational incidents.
- Long-Term Value: The final phase of Continuous Improvement, featuring bi-weekly cost analysis and regular security audits, ensures the environment’s security and cost effectiveness are maintained indefinitely.
4. Conclusion
We implemented a phased solution using AWS Control Tower to establish a secure, multi-account architecture with dedicated OUs for management, security, and environments. Core security tools like GuardDuty, Security Hub, and Inspector were deployed across all accounts, resulting in zero critical security findings. Financial predictability was immediately achieved by implementing AWS Budgets and Cost Anomaly Detection, eliminating unexpected bills. This transformation established a scalable, well-governed, and financially predictable cloud foundation, replacing ad-hoc operations with formalized, continuous processes.








